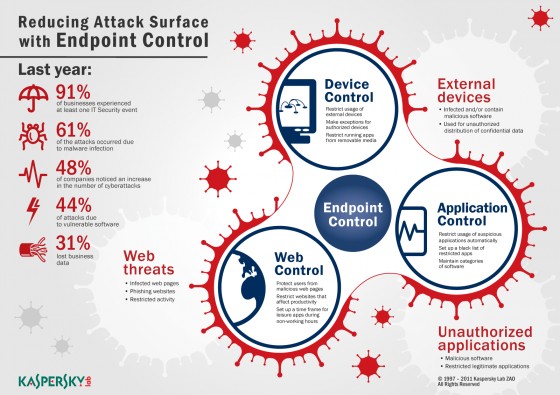
POST: The
attack surface of a software environment is the
sum of the different points (the "attack vectors") where an
unauthorized user (the "attacker") can try to
enter data to or
extract data from an environment.
what is available to be used by an attacker against the product itself.
||
No comments:
Post a Comment
You will get Reply with in 24 hours